|
|
You probably need an Internet Security Suite. Both Windows and Mac users need it. I don’t know of a good Internet Security Suites for Linux. But, if you’re running Linux, you are probably already fairly computer savvy. An Internet Security Suite usually has a number of components to protect you against different dangers from hackers:
- A software firewall. This blocks most of the unsolicited inbound hacking traffic from reaching your computer. Sometimes, it can also block outbound traffic.
- An antivirus program. If you are running any program that asks for content from the Internet (email, browsing, downloads, watching movies, etc.), the content coming into your computer may have malware inside it. Most antivirus programs will check the incoming content from the Internet, and scan for malware. If it finds malware, it will block it from running or quarantine it. All antivirus programs that I know of can also scan your entire hard disk, looking for malware that is already installed, and try to quarantine and/or remove any malware it finds.
- An anti-spam filter. I hate spam. You probably do too. The only way to reduce your spam is to install some kind of an anti-spam filter. If you are only doing webmail, this probably doesn’t affect you. Gmail has an anti-spam filter that you don’t ever see
- A privacy filter. You can configure this with your credit card numbers, and if the privacy filter sees your credit card number being sent out from your computer, it can stop it (sometimes).
- Parental Control software: This prevents your kids from browsing to inappropriate sites.
- A backup program: If your computer gets totally hosed, sometimes, your only alternative is to restore from a backup. To restore from a backup, you have to have a backup in the first place…
- Performance tuning: This is a nice-to-have, but not essential.
Remember: computer security is like a cat-and-mouse game, or a game of one-upmanship. The good guys try to keep malware from getting onto your computer, the bad guys try to get around that protection, the good guys make their protection better, the bad guys try to get around the newer protection, etc.Don’t get the impression that you can install an Internet Security Suite, and then you are protected, and can do anything you want to on your computer. You still need to practice other computer security measures too.
Here’s how to get an Internet Security Suite:
- See if your ISP will provide security software for free. (Comcast does.)
- Otherwise, buy an Internet Security Suite. Here are some recommendations: http://www.consumersearch.com/internet-security-software
- Run a full system scan. Allow the security suite to fix any issues it discovers.
- If you want an added layer of protection, there is another security scanner I run called Malwarebytes Antimalware.
- Microsoft has a free security suite called Microsoft Security Essentials.
Hopefully, you are doing this as a precautionary measure, and your computer isn’t infected. But what should you do if your computer is infected? Try the steps above. If your computer still doesn’t work, here are some options:
- Engage the Geek Squad (you might get lucky),
- Rebuild your computer (beware, this is a ton of work), or
- Buy a new computer, and transfer your old files to your new computer (if your computer is truly infected beyond repair, this is probably your best option).
- Optional: once you moved everything you care about to your new computer, you can rebuild your old one. It will be easier now, because you don’t have to worry about saving personal files. Then you will have two computers, and you can keep one disconnected from the Internet, and put your top-secret files on that computer.
Part of security maintenance is making sure that your software gets the latest updates. If you have a Windows computer, there is a great software package that will help you do this: Personal Software Inspector (PSI). For Windows users, I recommend that you download and install this program right away.
Secunia PSI inventories the software on your PC, and checks it against a list of known security vulnerabilities. It can automate the patching of some programs. For your personal computer, the personal version of their software is free. If you are a corporate user, you should license the corporate version of their software, and make sure it is installed on every PC in your company. Then, thank the people at Secunia for doing what they do (it is SO important), and thank God that there are people in the world, like the folks at Secunia, working so hard to keep you safe.
What to do:
a) Make sure you have Automatic Updating enabled:
- For Windows PCs: http://windows.microsoft.com/en-us/windows/turn-automatic-updating-on-off#turn-automatic-updating-on-off=windows-7
- For Macs: http://www.macworld.com/article/1164882/how_to_adjust_os_x_s_software_update.html
b) For Windows, download and install Secunia PSI (http://secunia.com/vulnerability_scanning/personal/) Corporate users? Buy it.
c) For Mac users, open System Preferences, go to Software Update, and schedule daily software checks and updates. I don’t know of any additional software like Secunia PSI for Macs.
If a software package is installed on your computer, some hacker out there has probably already figured out a new security vulnerability for that software. If the vulnerability is so new, that there is no patch to fix it, it is called a “zero-day” vulnerability. So, the best way to stay secure is… drum roll please… don’t install the software. Yes, you heard me right. If you don’t need it, don’t install it. If the software is not on your system, it can’t be exploited, and it doesn’t need to be patched.
Here’s how to uninstall software you don’t use:
- For Windows: http://windows.microsoft.com/en-us/windows/uninstall-change-program#uninstall-change-program=windows-7
- For Macs: http://guides.macrumors.com/Uninstalling_Applications_in_Mac_OS_X
You can read more here about choosing software and downloading software safely.
The main reason to upgrade is that the newer versions of Windows and Mac OS X implement something called a security sandbox.
Suppose you get hungry, and want a recipe for a sandwich. So, you download some recipe software, install it, download a recipe for a sandwich, and make yourself a sandwich. If you accidentally chose a recipe program that is malicious, while you have been making your sandwich, your recipe program could access your Quicken data, send it to HACKERS_R_US.COM, where hackers decode the Quicken file, obtain your banking passwords, and login to the your banks website as you, and write themselves a check.
What? My recipe program can access my Quicken data? Yes (if you use the same login all the time). That’s why you put Quicken on your top-secret computer (always disconnected from the Internet), and your recipe program on your online computer. Unless of course your secret plan to become a billionaire involves making killer scones to sell at Starbucks. In that case, you would want the recipe program (with your FABULOUS scone recipes) on your top-secret computer too. 🙂
Basically, if you are using the same login, all your programs can access the data of all your other programs. A more accurate, detailed description of the problem is in my blog article here: All Your Programs Can Access Your Quicken Data. Microsoft’s comment about this is: “An authenticated user can see all of their documents, and so can the running programs. This is the basic security design of Windows, and not something we intend to change.”
Think about that for a minute. That’s why you shouldn’t just install anything you find on the Internet. For example, one fake Android app steals data and then chastises you for trying to get around paying for the real app!
Now, how can we address this?
For Windows, you need to be running Windows 8 or later. You also need to limit yourself to applications that you can purchase through the Windows App Store. Why is that? To be advertised in the Windows App Store, Windows developers have to implement something called a security sandbox. If you download and install any application from somewhere else, there is no guarantee that the software does that.
“Windows Store apps are very different from Windows Desktop apps. Windows Store apps follow in the footsteps of iOS and Android development, providing a relatively small instruction set, a deployment and lifecycle model, and a sandbox for execution.”
So, Windows Store apps have a security sandbox for execution. That’s good. What about Windows Desktop apps, the Windows apps that you know and love and have already purchased? They use the older security rules, so the problem described above applies to them too. If you’re logged in as the same user, every Windows Desktop app can access all the data of every other Windows Desktop app. Ugh.
On the surface, the situation with Apple Macs is not much different. For Macs, you need to be running Mac OS X Mountain Lion (10.8 or later) to get the sandbox technology. You also need to limit yourself to applications that you can purchase through the Apple App Store, for a similar reason. Remember all the Mac programs that you know and love and have already purchased? They use the older security rules, so the problem described above applies to them too. Ugh.
I heard from a friend of mine, Paul Adams, who is very knowledgeable about Apple products: His comments:
a) All apps purchased through the app store for Mac OS X are sandboxed. It’s a requirement for developers who submit apps to the store to support it.
b) Look at the “gatekeeper” in Mac OS X 10.8 as well. It checks apps you install from the internet and will only let you run apps from “Trusted Developers” (an online list maintained by Apple). This is a medium type security setting for people who don’t want to be restricted to only the app store downloads but want to have some restrictions from the free-wheeling internet.
If you want to upgrade to Mac OS X Mountain Lion (10.8), it may not be as easy as you think. I have a Mac at home that my wife uses. We bought it in 2006. It still works just fine, thank you. Being security conscious, I wanted to upgrade to Mountain Lion (10.8). I upgraded to Mac OS X Lion (10.7) earlier, and it was pretty easy. No issues. So, I looked at the hardware requirements for Mountain Lion, and my Mac met the hardware requirements. It was older, but I thought it is had the right hardware, so it should work OK. When I tried to upgrade, it said it wouldn’t work for my computer. Are there some additional hardware requirements that are not listed? Not sure about this one, and I’m not too pleased that I have to buy a new Mac to run Mountain Lion.
What to do:
a) Upgrade your old computers to the latest version of the OS (Windows, OS X, etc.). If you can do that, you can benefit from the new security features.
b) For Windows, update to Windows 8 or later, and purchase and run only apps from the Windows App Store.
c) For Mac OS X, update to Mac OS X Mountain Lion (10.8) or later, and purchase and run only apps from the Apple App Store.
d) Don’t worry about Apple iPads and iPhones as much. Those devices are running Apple iOS, which requires all programs to run in a security sandbox.
e) For Linux, I don’t know of a similar easy way to implement sandboxing. (Don’t get me wrong. I love Linux. I use it every day, and the company where I work runs large businesses on Linux.) Linux has plenty of security mechanisms, but I don’t know of an easy way to implement sandboxing.
f) If you don’t have the extra cash to spend on new hardware and software, take a look at Ubuntu. Ubuntu is the most consumer friendly version of Linux. It is free to download, and you can also download hundreds of free Linux apps, including a free office suite. It won’t have all the latest Microsoft or Apple security changes, but for a second computer, it would certainly be cheap.
One way to improve your computer security is to ditch your old computer and buy a new one with new software. Why? Because computer security is like the arms race. Hackers are working to discover new software vulnerabilities all the time. If they find a good one, they may exploit it, or sell it to somebody else. On the other side of the fence, software vendors are trying really hard to fix those vulnerabilities, and also other vulnerabilities they discover via their own internal testing. So, it’s like a cat and mouse game. It’s also like terrorists and the TSA. Pity the poor TSA worker who has to try to plug ALL the ports of entry that a terrorist could use to jump on a plane, while the terrorist only has to find ONE weakness, and exploit it. Computer security is just like that.
So, Microsoft, Apple, and the Linux folks are always coming up with new versions of their operating systems (Windows, OS X, various Linux distributions) that are more secure that the old versions of the software. So, if you want the latest in computer security protection– such as security sandboxes– you need to upgrade.
For Microsoft users, another good reason to update is the arrival of IE10. IE10 has some new security features that you should activate. But, you can only get IE10 on Windows 7 and Windows 8. If you’re running Windows XP or Windows Vista, you’re out of luck. Also, if you’re running Windows XP, your patch support will END on April 8, 2014. That is when Microsoft will officially stop supporting Windows XP. Any remaining vulnerabilities will not be patched, and at least one blog I’ve seen says that hackers are saving all their zero-day bugs until April 9th, so they can have a field day. Don’t wait. Bite the bullet, and upgrade. You need the new security features anyway.
What to do:
a) If you can’t upgrade your old computers, unplug them from the Internet, and use them to store your top-secret documents.
b) Make sure you upgrade or replace (preferably replace) Windows XP computers BEFORE April 9th, 2014.
c) Buy a new computer, and use that for your Internet browsing.
First of all, you DID turn on encryption for your wireless network, didn’t you? If you wireless network is unencrypted, then anyone driving by can connect to your network, and try to steal information from your computers. (This is called wardriving. And, there is a newer version where the bad guys can do the same thing with radio controlled airplanes. At a DEF CON hacker conference, they even have a wardriving competition! Ugh. If you’re a security geek, you probably already attend a DEF CON or Black Hat conference. I’ve never been to one, but I’m sure it would be interesting, sobering, and make me never want to get near a computer again. That would be a problem for me, since I work as a computer database administrator.) The first thing you should know about wireless networks is that you must TURN ON the encryption.
The second thing you need to know about wireless networks is that the old encryption algorithms have already been broken, and you can download software to figure out somebody else’s wireless network password (or even your own). Here are some tips for securing your wireless network. If your wireless router does not support WPA2-AES, throw it away (or give it to someone that has interesting stuff on THEIR computers), and buy a new one that supports WPA2-AES. Check out Consumer Search. I recently bought a new Netgear WNDR3700, and this wireless router has a separate guest network from your private network; a nice-to-have optional feature.
Even if you have a wireless router that supports WPA2-AES, you still need to give it a good password. Generate a long, complex password and use that for your wireless network. I know it’s a hassle to type in an ugly, long password like that, but you only to type the password in once (for each computer you connect to your wireless network).
Here is another reason you should encrypt your wireless network: Google Street View. Google your address in Google Maps, and you can click on a photograph of your street, and see your house. (Hopefully, you weren’t wandering outside in your bathrobe to get the morning paper when the Google Street View car drove by and took your picture.) Did you know that Google was wardrving at the same time they were taking your picture? If you happened to have an unencrypted wireless network when the Google car drove by, Google connected to your network, and downloaded anything they could find.
What do you think of that? I was appalled when I found out about it. I’m not a lawyer, so I can’t comment on the legality of it, but I am human, and I have a certain expectations for ethical conducts, and in my opinion, Google crossed the line on this one. Google did not advertise that they were doing this, probably because they realized that there would be a huge uproar if people found out. Well, people did find out, and as a consequence, there is a huge uproar. Hey Google: don’t be evil. Hold yourself to a higher ethical standard, and assume that sneaky actions may someday be found out, and you will pay the consequences.
So, to summarize, here’s what you should do to protect your wireless network:
- Make sure your wireless router is newer, and supports the latest encryption protocols. WPA2-AES is the best there is right now.
- TURN ON encryption.
- Use a STRONG, LONG, RANDOM password to access your wireless network.
- If you’re curious, here are more ideas for securing your wireless network.
- If you are mad about Google crossing the ethical line with Google Street View wardriving, contact them, and let them know how you feel about it.
Devices that provide hardware firewalls usually need to be configured. It may be that the default factory settings are OK, and you don’t need to do anything extra. But, it would be good to contact your ISP, and ask if they have instructions for configuring your firewall with high security.
For example, I just installed a wireless router for my mother-in-law. The wireless router ( a ZyXEL PK5001Z) was supplied by and configured by her ISP (CenturyLink). It had a hardware firewall built into it. When I checked the configuration pages, I found that the default security settings were more lax than I would want. To be honest, I can’t remember if it was blocking unsolicited inbound packets or not. But, I do remember that the default security settings were pretty lax. So, I configured it more securely. During some troubleshooting, I had to reset the router to factory settings, and then the security options were lax again. Ugh. Time to reconfigure…
Now, CenturyLink knows about network security (all ISPs do). They have a division of their business that caters specifically to network security. For small businesses, CenturyLink will manage your network. (I found this while googling about other security topics – it was a paid-for banner ad at the top of my search results.) For large businesses, CenturyLink has an entire smorgasbord of network security offerings. But, for the average homeowner just wanting Internet connectivity, it’s harder for CenturyLink to offer the service and stay profitable, so they will opt to configure things so that people don’t complain and call their support desk, and that usually means lax security. If you want more security, you will need to explicitly configure your device to do that.
The US Government CERT website has some really good references here:
What to do:
a) If your ISP provided a hardware firewall (or some other networking hardware that has a firewall built into it), contact them, and ask for instructions for how to securely configure your hardware firewall.
b) If your ISP DID NOT provide you a hardware firewall, call your ISP, and give them an earful for letting your computer get infected. Then, go buy a hardware firewall, or a wireless router that has a firewall built into it.
c) Get someone to help you install it and configure it. You may need your ISP to help you on this one, because router configuration can be tricky.
Firewalls are filters that keep the most of the bad Internet traffic out. There are two types of firewalls: hardware firewalls (a separate box you plug in between your computer and the Internet) and software firewalls (software that you install on your computer). You should be using BOTH types, but this post focuses on hardware firewalls.
Why do you need a hardware firewall? Suppose you buy a new computer, and it has the latest Microsoft Windows operating system (or Apple’s OS X, or Linux, or whatever) on it. Before you plug it in, it already has software vulnerabilities. Why? Because there is a lag time between when your computer was built and when it was delivered to you. In contrast, hacking attacks happen almost constantly, and software vulnerabilities are being discovered and patched very frequently.
So, what do you do? Plug it into the Internet? NO! First, read 10 Ways to Improve the Security of a New Computer (developed and published by CERT). If you don’t have a hardware firewall blocking the bad traffic, the statistics are that you have about 4 minutes to download and install your initial batch of patches before your new computer gets infected. 4 minutes! Pretty surprising, huh? If you don’t believe me, check out:
Your ISP (e.g. Comcast, etc.) didn’t tell you that that a hardware firewall is a CRITICAL and REQUIRED component for your Internet hookup? Shame on them. Contact your ISP, and ask whether or not their Internet hookup kit includes a hardware firewall. Many wireless routers have a firewall already built in. If yours does, great! Just make sure it is configured correctly.
If you think your new computer is infected…
- Immediately disconnect your computer from the internet.
- Call your ISP, and ask if they provided a hardware firewall to you (or told you to buy one). If not, give them an earful for allowing your computer to get infected.
- Implement an Internet Security Suite.
- Make sure you have a hardware firewall.
- Make sure it is installed and configured correctly. You may need your ISP to help you on this one.
- Plug your fixed-up computer back into your newly secured network.
If all this is too much for you, you can buy technical help. Of course, there may be someone you know who can help you– I’m the tech support guy for my entire extended family. Whatever it takes, just get it done. The WORST thing you can do is NOT install a hardware firewall, or some other device like a wireless router that has a firewall built in.
I don’t know about you, but I don’t have any top-secret documents. But, suppose you use Quicken. Suppose you have a secret plan to become the world’s next billionaire. Suppose you don’t want the NSA prying into the photo collection of your, um, kids. Well, don’t connect your computer to the Internet.
Some people may think this is a little extreme. But here’s the truth: the ONLY 100% guaranteed way to keep top-secret data safe is to isolate it from the internet. (Kind of like abstinence is the only 100% guaranteed way to prevent pregnancy.) Computer security is an arms race between hackers and developers, and no matter how vigilant you are, there’s just no telling what they will come up with next.
Remember Mister Rogers telling kids about watching TV: If there is something scary on TV, you can turn it off . Apply the same principle to the Internet: If there is something scary on the Internet (there is), you can simply disconnect. Or, if you feel like you have to connect, connect for a very short time, then disconnect when you are done. The less time you are connected to the Internet, the better (at least on your PC that has sensitive information on it).
For companies that handle extremely sensitive data (such as medical records which are protected by HIPPA), it makes sense to store these records on a separate internal server. But what about individuals just trying to protect stuff on their home computers?
Here is one possibility: buy two computers, one to connect to the Internet, and one to keep off the Internet. Computers are relatively cheap nowadays. Put your sensitive information on the computer that never connects to the Internet. If you consider your financial data sensitive (you want to keep it private), do your Quicken on that computer, and then close Quicken. Swivel in your chair, and start typing on your computer that connects to the Internet, and browse to your favorite websites. If you want some software on your top-secret PC, and it is available as a download, download the software on your Internet-connected PC, and use “sneaker net” to transfer the download to your top-secret PC.
If you can’t afford two computers, consider keeping your most sensitive files on an external hard drive, or even a USB drive, instead of your PC. Only plug the external drive into your computer when your computer is offline.
If the computer or drive which stores your top secret files never connects to the Internet, you don’t need to worry about anyone accessing the data, not even the NSA (unless they break into your home and steal your computer). If you want to protect even against that, get some type of hard-disk encryption. If you encrypt your hard disk, you will be able to read it and use it (with the appropriate password), but other people won’t. See some ideas in the “What to do” section below.
To access your encrypted hard-disk, you will need a password. Don’t forget that password. (My daughter had a classmate at Stanford who lost his encryption password and wasn’t able to access his thesis research. The archetypical absent-minded genius…) Write the password down somewhere, but hide the piece of paper so other people don’t find it. Don’t put it on a sticky note on the monitor; if the thief takes your monitor, they will have your password too.
Or, use KeePass, another great piece of free software for storing your passwords. Using KeePass, you can create a file of your passwords, and easily generate random, hard-to-guess passwords, one for each website you have an account at. You only have to remember one MASTER password.
Here are my recommendations for keeping top secret data safe:
a) Buy a new computer, and connect that to the Internet. It will have the newer security features, so it will be less likely to get infected. SEE BELOW for instruction for HOW to plug a new computer into the Internet so it won’t get infected right away.
b) Unplug your old computer from the Internet. If it is infected, the malware won’t be able to send any of your top-secret information anywhere (at least once it is unplugged), and you won’t inadvertently become part of a botnet.
c) If you want to encrypt your hard drive, check to see if your computer already supports it:
- For PCs: Bit Locker Drive Encryption
- For Macs: FileVault drive encryption
d) If your computer doesn’t come with built-in encryption, you still have a couple of options:
- For Linux, you can encrypt part of your hard disk with TrueCrypt
- If your PC or Mac doesn’t have built-in encryption, use TrueCrypt.
d) Don’t forget the encryption password. If you forget your encryption password, your encrypted data will be gone forever. Caveat: I have not encrypted my hard disk. It is not the highest thing on my list.
If you are hooked up to the Internet (at home, at a local coffee shop, at an airport, wherever), there is a constant barrage of Internet traffic trying to get to your PC. Hackers are trying to get into your computer. They might be in China, in Russia, in the US, in your own neighborhood, or even part of the US government (i.e. the NSA). The NSA has had such bad press lately (mostly due to the public disclosures made by Edward Snowden) that, yes, you should assume they’re trying to access your computer.
So, how many of these attacks are occurring every day? Way too many (see below). Why are hackers so determined? Because there are endless ways to monetize a hacked computer. Are they attacking YOU? Not usually. Hackers are scanning every Internet connection out there (not just yours). If you are connected to the Internet, and there is not a firewall (a network filter that prevents traffic that you don’t want) between you and the Internet, hackers are probing for weaknesses in your computer security.
Here is one way to visualize the problem: Akamai Technologies, Inc, a large Internet content delivery network, has a VERY COOL real-time Internet monitoring webpage. After you click on the link, you can choose Modes of: Attacks, Latency, and Traffic. “X” the box for Attacks, and you will see this:
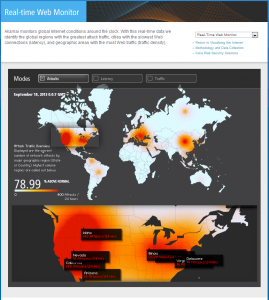
Not good, especially if you live in the Western US.
Here is another way to visualize the problem: My household has an Internet connection from Comcast (our local ISP). To determine how often I’m getting attacked, I can look at my firewall logs:
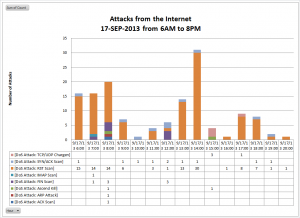
This is an Excel chart of the inbound packets that my firewall thought was an attack on 17 Sep. 2013. The frequency of the “attacks” varied tremendously, depending on the time of day. During the 2PM hour that day, I had 31 attacks (about 1 every 2 minutes). At the 10AM hour, there was only 1 attack for the entire hour. So, the “Hacking Attack Rate” varies significantly. Most people probably aren’t aware of this; it is happening more often than most people think. And it’s increasing every day.
The threat from network spying is great enough that the Kremlin is considering disconnecting their top-secret computers entirely. From the Huffington Post: “Pro-Kremlin newspaper Izvestia said the state service was looking to purchase 20 typerwriters because using computers to prepare top-secret documents may no longer be safe.” Hmmmm… They could just unplug their computers. But, the Kremlin folks are pretty smart. What do they know that I don’t know? Should I be buying a typewriter?
For my recommendations about how to protect yourself from ever-increasing hacking attacks, read:
|
|



Recent Comments